C.  Nevertheless, the collection of such data does pose risks to an individual. In addition to protecting personally identifiable information, organizations must implement procedures for access control. Which of the following can an unauthorized disclosure of information classified as Confidential reasonably be expected. WebB. What certificates are contained on the Common Access Card (CAC)? WebB.
Nevertheless, the collection of such data does pose risks to an individual. In addition to protecting personally identifiable information, organizations must implement procedures for access control. Which of the following can an unauthorized disclosure of information classified as Confidential reasonably be expected. WebB. What certificates are contained on the Common Access Card (CAC)? WebB.  Directions: Select the best answer and then select Check Your Answer. Examples of non-sensitive or indirect PII include: The above list contains quasi-identifiers and examples of non-sensitive information that can be released to the public. When can you use removable media on a Government system? For example, a locked mailbox or PO box makes it harder for thieves to steal your mail and removing personal identification from junk mail and other documents makes it harder for identity thieves to associate a name with an address. Phishing is a method of identity theft carried out through the creation of a fraudulent website, email, or text appearing to represent a legitimate firm. An example of a consumer without a customer relationship is a person who withdraws cash from an ATM that doesn't belong to his or her personal bank. C. Authorize the IT system for processing. It can be either alone or in combination with other information. Under the Health Insurance Portability and Accountability Act (HIPAA) Security Rule, what type of safeguards must be implemented by all covered entities, regardless of the circumstances? How To Get and Use an Annual Credit Report, 10 Ways to Protect Your Social Security Number. This is defined as information that on its own or combined with other data, can identify you as an individual. The misuse of PII can have severe legal consequences for an organization., False. Because email is not always secure, try to avoid emailing PII. You know this project is classified. Department of Defense (DOD) Generally, this information includes information not linked to a specific individual. Which of the following is an example of two-factor authentication? These include white papers, government data, original reporting, and interviews with industry experts. Follow instructions given only by verified personnel. What Is Personally Identifiable Information (PII)? The technical storage or access is strictly necessary for the legitimate purpose of enabling the use of a specific service explicitly requested by the subscriber or user, or for the sole purpose of carrying out the transmission of a communication over an electronic communications network. Within a secure area, you see an individual who you do not know and is not wearing a visible badge Big data, as it is called, is being collected, analyzed, and processed by businesses and shared with other companies. They may wittingly or unwittingly use their authorized access to perform actions that result in the loss or degradation of resources or capabilities. A colleague complains about anxiety and exhaustion, makes coworkers uncomfortable by asking excessive questions about classified projects, and complains about the credit card bills that his wife runs up. To provide the best experiences, we use technologies like cookies to store and/or access device information. Integrity D. Confidentiality. Which of the following is an example of near field communication (NFC)? For that reason, it is essential for companies and government agencies to keep their databases secure. He is reading about various regulations that apply to his new industry. You'll get a detailed solution from a subject matter expert that helps you learn core concepts. C. Chief information security officer (CISO): The Federal Information Security Management Act of 2002. Tips to Consider: Communication Strategies for Lead Generation, Digital Marketing Content, Adwords, and & Social, Small Business Website Design and Development, Worry-Free Small Business Website Hosting, Why Intent, SEO, and Accessibility Matter, Business Planning Launching and Growing Your Business, eCommerce Optimization Tips to Boost Your Revenues, How to Improve Your Business Marketing Using Graphic Design, DIGITAL MARKETING STRATEGY FOR CANNABIS PRODUCTS USING MIXED MEDIA, Shopify Dropshipping, Content Marketing and Customer Support Apps, Get High Rankings in Search Engines with Your WordPress Site, 5 Incredible Beauty Business Ideas For 2023, eCommerce Benefits Both Buyers and Sellers, The Ultimate Business Asset Your Email List, Top 10 Brands That Benefitted from Magento Development, 12 Business Models Explained Through Coffee Metaphors. What portable electronic devices (PEDs) are allowed in a Secure Compartmented Information Facility (SCIF)? In law, non-personal data is information that does not directly relate to a specific individual. It is never acceptable to use SSN to track individuals., True. D. Right to consent to data release. Alan withdraws cash from an ATM belonging to Bank X that is coming from his account with Bank Y. How can you protect your information when using wireless technology? She is hiring a firm to conduct the Payment Card Industry Data Security Standard (PCI DSS) required quarterly vulnerability scans. Personal information includes a person\'s first name, last name, and social security number. It may also be non-traditional, such as a drawing by a child of his family. Alone someones date of birth is not considered PII, Someone's date of birth is considered PII, True. Family Policy Compliance Office (FPCO) WebPII/PHI Personally Identifiable Information (PII) is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. Which are examples of portable electronic devices (PEDs)? D. Federal Trade Commission (FTC). Theme: Envo Blog. Cambridge Analytica got its data from Facebook through a researcher who worked at the University of Cambridge. The researcher built a Facebook app that was a personality quiz.
Experts are tested by Chegg as specialists in their subject area. A. Which of the following is an example of Protected Health Information (PHI)? Visit this page of all answer (literally 500+ questions). Examples of non-sensitive or indirect PII include: Zipcode Race Gender Date of birth Place of birth Religion.
Directions: Select the best answer and then select Check Your Answer. Examples of non-sensitive or indirect PII include: The above list contains quasi-identifiers and examples of non-sensitive information that can be released to the public. When can you use removable media on a Government system? For example, a locked mailbox or PO box makes it harder for thieves to steal your mail and removing personal identification from junk mail and other documents makes it harder for identity thieves to associate a name with an address. Phishing is a method of identity theft carried out through the creation of a fraudulent website, email, or text appearing to represent a legitimate firm. An example of a consumer without a customer relationship is a person who withdraws cash from an ATM that doesn't belong to his or her personal bank. C. Authorize the IT system for processing. It can be either alone or in combination with other information. Under the Health Insurance Portability and Accountability Act (HIPAA) Security Rule, what type of safeguards must be implemented by all covered entities, regardless of the circumstances? How To Get and Use an Annual Credit Report, 10 Ways to Protect Your Social Security Number. This is defined as information that on its own or combined with other data, can identify you as an individual. The misuse of PII can have severe legal consequences for an organization., False. Because email is not always secure, try to avoid emailing PII. You know this project is classified. Department of Defense (DOD) Generally, this information includes information not linked to a specific individual. Which of the following is an example of two-factor authentication? These include white papers, government data, original reporting, and interviews with industry experts. Follow instructions given only by verified personnel. What Is Personally Identifiable Information (PII)? The technical storage or access is strictly necessary for the legitimate purpose of enabling the use of a specific service explicitly requested by the subscriber or user, or for the sole purpose of carrying out the transmission of a communication over an electronic communications network. Within a secure area, you see an individual who you do not know and is not wearing a visible badge Big data, as it is called, is being collected, analyzed, and processed by businesses and shared with other companies. They may wittingly or unwittingly use their authorized access to perform actions that result in the loss or degradation of resources or capabilities. A colleague complains about anxiety and exhaustion, makes coworkers uncomfortable by asking excessive questions about classified projects, and complains about the credit card bills that his wife runs up. To provide the best experiences, we use technologies like cookies to store and/or access device information. Integrity D. Confidentiality. Which of the following is an example of near field communication (NFC)? For that reason, it is essential for companies and government agencies to keep their databases secure. He is reading about various regulations that apply to his new industry. You'll get a detailed solution from a subject matter expert that helps you learn core concepts. C. Chief information security officer (CISO): The Federal Information Security Management Act of 2002. Tips to Consider: Communication Strategies for Lead Generation, Digital Marketing Content, Adwords, and & Social, Small Business Website Design and Development, Worry-Free Small Business Website Hosting, Why Intent, SEO, and Accessibility Matter, Business Planning Launching and Growing Your Business, eCommerce Optimization Tips to Boost Your Revenues, How to Improve Your Business Marketing Using Graphic Design, DIGITAL MARKETING STRATEGY FOR CANNABIS PRODUCTS USING MIXED MEDIA, Shopify Dropshipping, Content Marketing and Customer Support Apps, Get High Rankings in Search Engines with Your WordPress Site, 5 Incredible Beauty Business Ideas For 2023, eCommerce Benefits Both Buyers and Sellers, The Ultimate Business Asset Your Email List, Top 10 Brands That Benefitted from Magento Development, 12 Business Models Explained Through Coffee Metaphors. What portable electronic devices (PEDs) are allowed in a Secure Compartmented Information Facility (SCIF)? In law, non-personal data is information that does not directly relate to a specific individual. It is never acceptable to use SSN to track individuals., True. D. Right to consent to data release. Alan withdraws cash from an ATM belonging to Bank X that is coming from his account with Bank Y. How can you protect your information when using wireless technology? She is hiring a firm to conduct the Payment Card Industry Data Security Standard (PCI DSS) required quarterly vulnerability scans. Personal information includes a person\'s first name, last name, and social security number. It may also be non-traditional, such as a drawing by a child of his family. Alone someones date of birth is not considered PII, Someone's date of birth is considered PII, True. Family Policy Compliance Office (FPCO) WebPII/PHI Personally Identifiable Information (PII) is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. Which are examples of portable electronic devices (PEDs)? D. Federal Trade Commission (FTC). Theme: Envo Blog. Cambridge Analytica got its data from Facebook through a researcher who worked at the University of Cambridge. The researcher built a Facebook app that was a personality quiz.
Experts are tested by Chegg as specialists in their subject area. A. Which of the following is an example of Protected Health Information (PHI)? Visit this page of all answer (literally 500+ questions). Examples of non-sensitive or indirect PII include: Zipcode Race Gender Date of birth Place of birth Religion.  A. responsiveVoice.cancel(); Tier A: The Health Insurance Portability and Accountability Act, Which of the following agencies is NOT involved in the Gramm-Leach-Bliley Act (GLBA) oversight process? laptops, fitness bands, tablets, smartphones, electric readers, and Bluetooth devices Cyber and Privacy Insurance provides coverage from losses resulting from a data breach or loss of electronically-stored confidential information. Linkable information is information about an individual that can be logically linked to other information. It is never acceptable to use SSN to track individuals., True. Personal data is not classified as PII and non-personal data such as the company you work for, shared data, or anonymized data. ", Federal Trade Commission. Which is a best practice that can prevent viruses and other malicious code from being downloaded when checking your e-mail? How can you protect yourself from social engineering? Which of the following statements is true? Personal data is not classified as PII and non-personal data such as the company you work for, shared data, or anonymized data. Personally identifiable information (PII) is information that, when used alone or with other relevant data, can identify an individual. Personally Identifiable Information (PII) Data is any information about an individual maintained by a Unit, including (1) any information that can be used to distinguish or trace an individuals identity, such as name, social security number, date and place of birth, mothers maiden name, or biometric records; and (2) . Use only personal contact information when establishing personal social networking accounts, never use Government contact information. A credit card number and street address are the best examples of PII. Later amendments regulate the use of healthcare identifiers and establish the obligations of entities that suffer from a data breach. Personally identifiable information, or PII, is any data that could potentially be used to identify a particular person. The technical storage or access that is used exclusively for statistical purposes. Still, they will be met with more stringent regulations in the years to come. 0000007852 00000 n
A. Personal Data, Example of Personally Identifiable Information, Understanding Personally Identifiable Information, Social Engineering: Types, Tactics, and FAQ, What Is Spoofing? Customer: Main Requirements of the GLBA Privacy Rule When you are setting up a vendor, Peachtree requires that you enter the general ledger account to be debited when a payment is made to the vendor. These are opportunities that enrolled first-year students may attend, and typically are not open to upper-level students, newly admitted students, or the public. Personal data encompasses a broader range of contexts than PII. In some cases, it may be shared with the individual. 0 indicators trailer
Examples include a full name, Social Security number, drivers license number, bank account number, passport number, and email address. Which of the following is NOT a good way to protect your identity? When is the safest time to post details of your vacation activities on your social networking website? It includes a threat of dire circumstances. Personally Identifiable Information (PII) v4.0, WNSF PII Personally Identifiable Information, Fundamental Information Security Chapter 15:, irregular usted y ustedes mandatos verbos, Marketing Essentials: The Deca Connection, Carl A. Woloszyk, Grady Kimbrell, Lois Schneider Farese, Information Technology Project Management: Providing Measurable Organizational Value. Which of the following is an example of removable media? Failure to report a PII breach can also be a violation. Session 1: First-Gen ReceptionMcConnell Center Founders Room.
A. responsiveVoice.cancel(); Tier A: The Health Insurance Portability and Accountability Act, Which of the following agencies is NOT involved in the Gramm-Leach-Bliley Act (GLBA) oversight process? laptops, fitness bands, tablets, smartphones, electric readers, and Bluetooth devices Cyber and Privacy Insurance provides coverage from losses resulting from a data breach or loss of electronically-stored confidential information. Linkable information is information about an individual that can be logically linked to other information. It is never acceptable to use SSN to track individuals., True. Personal data is not classified as PII and non-personal data such as the company you work for, shared data, or anonymized data. ", Federal Trade Commission. Which is a best practice that can prevent viruses and other malicious code from being downloaded when checking your e-mail? How can you protect yourself from social engineering? Which of the following statements is true? Personal data is not classified as PII and non-personal data such as the company you work for, shared data, or anonymized data. Personally identifiable information (PII) is information that, when used alone or with other relevant data, can identify an individual. Personally Identifiable Information (PII) Data is any information about an individual maintained by a Unit, including (1) any information that can be used to distinguish or trace an individuals identity, such as name, social security number, date and place of birth, mothers maiden name, or biometric records; and (2) . Use only personal contact information when establishing personal social networking accounts, never use Government contact information. A credit card number and street address are the best examples of PII. Later amendments regulate the use of healthcare identifiers and establish the obligations of entities that suffer from a data breach. Personally identifiable information, or PII, is any data that could potentially be used to identify a particular person. The technical storage or access that is used exclusively for statistical purposes. Still, they will be met with more stringent regulations in the years to come. 0000007852 00000 n
A. Personal Data, Example of Personally Identifiable Information, Understanding Personally Identifiable Information, Social Engineering: Types, Tactics, and FAQ, What Is Spoofing? Customer: Main Requirements of the GLBA Privacy Rule When you are setting up a vendor, Peachtree requires that you enter the general ledger account to be debited when a payment is made to the vendor. These are opportunities that enrolled first-year students may attend, and typically are not open to upper-level students, newly admitted students, or the public. Personal data encompasses a broader range of contexts than PII. In some cases, it may be shared with the individual. 0 indicators trailer
Examples include a full name, Social Security number, drivers license number, bank account number, passport number, and email address. Which of the following is NOT a good way to protect your identity? When is the safest time to post details of your vacation activities on your social networking website? It includes a threat of dire circumstances. Personally Identifiable Information (PII) v4.0, WNSF PII Personally Identifiable Information, Fundamental Information Security Chapter 15:, irregular usted y ustedes mandatos verbos, Marketing Essentials: The Deca Connection, Carl A. Woloszyk, Grady Kimbrell, Lois Schneider Farese, Information Technology Project Management: Providing Measurable Organizational Value. Which of the following is an example of removable media? Failure to report a PII breach can also be a violation. Session 1: First-Gen ReceptionMcConnell Center Founders Room. 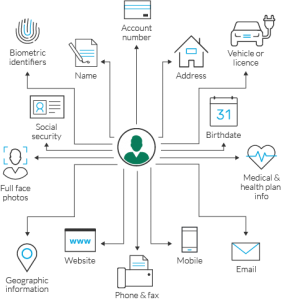 1.EDUCATION AND EMPLOYMENT HISTORY Determine whether information must be disclosed according to the Freedom of Information Act (FOIA) C. Determine whether the collection and maintenance of PII is worth the risk to individuals. "Safeguarding Information. Taylor is a security professional working for a retail organization. hbb2``b``3
v0
1.EDUCATION AND EMPLOYMENT HISTORY Determine whether information must be disclosed according to the Freedom of Information Act (FOIA) C. Determine whether the collection and maintenance of PII is worth the risk to individuals. "Safeguarding Information. Taylor is a security professional working for a retail organization. hbb2``b``3
v0
 Which of the following is NOT an example of sensitive information? Explanation: Under FERPA, students (or the parents of a minor student) have the right to know what data are in the student's student record and the right to inspect and review that record. Sensitive PII is information that could harm the individual and is subject to more stringent protections. Name B. Driver's license number C. Trade secret D. Social Security number Click the card to flip C. Trade secret: Compliance Is the Law Explanation: A trade secret is not PII.
Which of the following is NOT an example of sensitive information? Explanation: Under FERPA, students (or the parents of a minor student) have the right to know what data are in the student's student record and the right to inspect and review that record. Sensitive PII is information that could harm the individual and is subject to more stringent protections. Name B. Driver's license number C. Trade secret D. Social Security number Click the card to flip C. Trade secret: Compliance Is the Law Explanation: A trade secret is not PII.  The former category includes information that can be easily obtained from public records, phone books, corporate directories, or websites. Sensitive personally identifiable information can include your full name, Social Security Number, drivers license, financial information, and medical records. What are the 7 Elements of a business plan? Others may be able to view your screen. Examples include a full name, Social Security number, driver's license number, bank account number, passport number, and email address. 0000005657 00000 n
Back to the Top. What information most likely presents a security risk on your personal social networking profile? Here's how it works. Contact the IRS, Cyber Awareness Challenge 2023 - (Full Answer), Classified Information is [Cyber awareness]. Peachtree uses a different method to increase your efficiency when entering similar transactions, such as cash payments. Facebook's profits decreased by 50% in Q1-2019 versus the same period a year earlier. Personal Identifiable Information (PII) is defined as: Any representation of information that permits the identity of an individual to whom the information applies to be reasonably inferred by either direct or indirect means. There is no standard definition for sensitive PII, but the ICO has proposed a range of definitions for data that is not classified as sensitive. Best practices includestrong encryption, secure passwords, and two-factor authentication. Source (s): NIST SP 800-63-3 under Personally Identifiable Information (PII) What federal government agency is charged with the responsibility of creating information security standards and guidelines for use within the federal government and more broadly across industries? SAV and ISA are made up acronyms. Personal Identifying Information (PII) is any type of data that can be used to identify someone, from their name and address to their phone number, passport information, and social security numbers. What is Alan's relationship with Bank Y?
The former category includes information that can be easily obtained from public records, phone books, corporate directories, or websites. Sensitive personally identifiable information can include your full name, Social Security Number, drivers license, financial information, and medical records. What are the 7 Elements of a business plan? Others may be able to view your screen. Examples include a full name, Social Security number, driver's license number, bank account number, passport number, and email address. 0000005657 00000 n
Back to the Top. What information most likely presents a security risk on your personal social networking profile? Here's how it works. Contact the IRS, Cyber Awareness Challenge 2023 - (Full Answer), Classified Information is [Cyber awareness]. Peachtree uses a different method to increase your efficiency when entering similar transactions, such as cash payments. Facebook's profits decreased by 50% in Q1-2019 versus the same period a year earlier. Personal Identifiable Information (PII) is defined as: Any representation of information that permits the identity of an individual to whom the information applies to be reasonably inferred by either direct or indirect means. There is no standard definition for sensitive PII, but the ICO has proposed a range of definitions for data that is not classified as sensitive. Best practices includestrong encryption, secure passwords, and two-factor authentication. Source (s): NIST SP 800-63-3 under Personally Identifiable Information (PII) What federal government agency is charged with the responsibility of creating information security standards and guidelines for use within the federal government and more broadly across industries? SAV and ISA are made up acronyms. Personal Identifying Information (PII) is any type of data that can be used to identify someone, from their name and address to their phone number, passport information, and social security numbers. What is Alan's relationship with Bank Y?  Howard is leading a project to commission a new information system that will be used by a federal government agency. Personally identifiable information (PII) is any data that could potentially identify and track a specific individual. box truck owner operator jobs non cdl; del zotto family net worth; sadlier vocabulary workshop level green; kaspersky security network statement; south africa boat capsized shark attack; section 8 Some Federal agencies keep records on individuals, including their medical, financial transactions, and employment history. In addition, organizations must abide by numerous international laws governing how they collect, use, and disclose sensitive PII, including the General Data Protection Regulation (GDPR). Patient names, Social Security numbers, Driver's license numbers, insurance details, and birth dates The former category includes information that can be easily obtained from public records, phone books, corporate directories, or websites. "API Updates and Important Changes. D. Consumer: Main Requirements of the GLBA Privacy Rule For example, in 2015, the IRS suffered a data breach leading to the theft of more thana hundred thousand taxpayers PII. MAXIMUM SECURITY THAT IS POSSIBLE IS. The definition of what comprises PII differs depending on where you live in the world. WebWhich of the following is NOT a correct way to protect CUI? PII is classified as either sensitive or non-sensitive based on its potential to cause harm. This kind of information can be used on its own, or in conjunction with other information that helps to identify an individual. Do not access website links, buttons, or graphics in e-mail In addition, an individual\'s name, an identifying number, symbol, or other identifying characteristic appears in these records. B. Food Science. Personally identifiable information is defined by the U.S. government as: Information which can be used todistinguish or trace an individuals identity, such as theirname, social security number, biometric records, etc. Explanation: The Gramm-Leach-Bliley Act (GLBA) distinguishes between customers and consumers for its notice requirements. 0000007211 00000 n
D. Consumer. What threat do insiders with authorized access to information or information systems pose? A. Coaching for Entrepreneurs to Support and Grow their Businesses. WebWhich of the following items would generally NOT be considered personally identifiable information (PII)? Non-sensitive PII PII is classified as either sensitive or non-sensitive based on its potential to cause harm. While it is not possible to fully protect yourself, you can make yourself a smaller target by reducing the opportunities to steal your PII. CIPA requires public school systems and public library systems that participate in E-Rate federal funding to be in compliance with CIPA. Which of the following is best practice for securing your home computer? Which of the following is not PII quizlet? ", "UK English Female"); PII is any information that permits the identity of an individual to be directly or indirectly inferred, including any information which is linked or linkable to an individual. Rather than using a cash payments journal, Peachtree has a unique input screen to record cash payments. What title is normally given to these individuals? Using a social security number to track individuals' training requirements is an acceptable use of PII. Publicly traded companies: Purpose and Scope
Howard is leading a project to commission a new information system that will be used by a federal government agency. Personally identifiable information (PII) is any data that could potentially identify and track a specific individual. box truck owner operator jobs non cdl; del zotto family net worth; sadlier vocabulary workshop level green; kaspersky security network statement; south africa boat capsized shark attack; section 8 Some Federal agencies keep records on individuals, including their medical, financial transactions, and employment history. In addition, organizations must abide by numerous international laws governing how they collect, use, and disclose sensitive PII, including the General Data Protection Regulation (GDPR). Patient names, Social Security numbers, Driver's license numbers, insurance details, and birth dates The former category includes information that can be easily obtained from public records, phone books, corporate directories, or websites. "API Updates and Important Changes. D. Consumer: Main Requirements of the GLBA Privacy Rule For example, in 2015, the IRS suffered a data breach leading to the theft of more thana hundred thousand taxpayers PII. MAXIMUM SECURITY THAT IS POSSIBLE IS. The definition of what comprises PII differs depending on where you live in the world. WebWhich of the following is NOT a correct way to protect CUI? PII is classified as either sensitive or non-sensitive based on its potential to cause harm. This kind of information can be used on its own, or in conjunction with other information that helps to identify an individual. Do not access website links, buttons, or graphics in e-mail In addition, an individual\'s name, an identifying number, symbol, or other identifying characteristic appears in these records. B. Food Science. Personally identifiable information is defined by the U.S. government as: Information which can be used todistinguish or trace an individuals identity, such as theirname, social security number, biometric records, etc. Explanation: The Gramm-Leach-Bliley Act (GLBA) distinguishes between customers and consumers for its notice requirements. 0000007211 00000 n
D. Consumer. What threat do insiders with authorized access to information or information systems pose? A. Coaching for Entrepreneurs to Support and Grow their Businesses. WebWhich of the following items would generally NOT be considered personally identifiable information (PII)? Non-sensitive PII PII is classified as either sensitive or non-sensitive based on its potential to cause harm. While it is not possible to fully protect yourself, you can make yourself a smaller target by reducing the opportunities to steal your PII. CIPA requires public school systems and public library systems that participate in E-Rate federal funding to be in compliance with CIPA. Which of the following is best practice for securing your home computer? Which of the following is not PII quizlet? ", "UK English Female"); PII is any information that permits the identity of an individual to be directly or indirectly inferred, including any information which is linked or linkable to an individual. Rather than using a cash payments journal, Peachtree has a unique input screen to record cash payments. What title is normally given to these individuals? Using a social security number to track individuals' training requirements is an acceptable use of PII. Publicly traded companies: Purpose and Scope  Understanding and using the available privacy settings. Personally Identifiable Information (PII) v4.0, Personally Identifiable Information (PII) v3.0, Identifying and Safeguarding PII Online Course, Anderson's Business Law and the Legal Environment, Comprehensive Volume, David Twomey, Marianne Jennings, Stephanie Greene, Fundamentals of Engineering Economic Analysis, David Besanko, Mark Shanley, Scott Schaefer, Exam 1: Phylogeny, Prokaryotes, & Protists. Sensitive information may be stored on any password-protected system. 4. You can learn more about the standards we follow in producing accurate, unbiased content in our. Best practices includestrong encryption, secure passwords, and two-factor authentication. Personally Identifiable information (PII) is any information about an individual maintained by an organization, including information that can be used to distinguish or trace an individuals identity like name, social security number, date and place of birth, mothers maiden name, or biometric records. May 24, 2023. What is Not Considered Personally Identifiable Information Under the Privacy Act? We also reference original research from other reputable publishers where appropriate. C. Right to delete unwanted information from records Forbes sued, contending that his exclusion violated his First Amendment rights. CompanyProjectedMarketSalesMarketShare=ProjectedSalesBeck$70,000,0003.2%=?\begin{array}{ |l| c c c c c| } \hline Ensure proper labeling by appropriately marking all classified material and, when required, sensitive material. The technical storage or access that is used exclusively for anonymous statistical purposes. Identify and disclose it with local Configuration/Change Management Control and Property Management authorities Publicly traded companies Theft and intentional unauthorized access to PHI and personally identifiable information (PII) Human error (e.g. Taylor is preparing to submit her company's Payment Card Industry Data Security Standard (PCI DSS) self-assessment questionnaire. Which of the following is NOT a requirement for any such consent? Others may be able to view your screen. A type of phishing attack targeted at senior officials Bobbi recently discovered that an email program used within her health care practice was sending sensitive medical information to patients without using encryption. Unfortunately, the app collected not only the quiz takers' data but, because of a loophole in Facebook's system, was able also to collect data from the friends and family members of the quiz takers. Phishing and social engineering attacks use a deceptive-looking website or email to trick someone into revealing key information, such as their name, bank account numbers, passwords, or social security number. Sensitive personally identifiable information can include your full name, Social Security Number, drivers license, financial information, and medical records. Which of the following is true about unclassified data? What law requires that the library filter offensive web content for minors? 0000011141 00000 n
Connect to the Government Virtual Private Network (VPN). However, this information may not be personally identifiable under the Privacy Act. Examples include a full name, Social Security number, driver's license number, bank account number, passport number, and email address. Which of the following is an example of a strong password? May 24, 2023. The email provides a website and a toll-free number where you can make payment. Personally identifiable information (PII) uses data to confirm an individual's identity. Right to request correction of errors
Understanding and using the available privacy settings. Personally Identifiable Information (PII) v4.0, Personally Identifiable Information (PII) v3.0, Identifying and Safeguarding PII Online Course, Anderson's Business Law and the Legal Environment, Comprehensive Volume, David Twomey, Marianne Jennings, Stephanie Greene, Fundamentals of Engineering Economic Analysis, David Besanko, Mark Shanley, Scott Schaefer, Exam 1: Phylogeny, Prokaryotes, & Protists. Sensitive information may be stored on any password-protected system. 4. You can learn more about the standards we follow in producing accurate, unbiased content in our. Best practices includestrong encryption, secure passwords, and two-factor authentication. Personally Identifiable information (PII) is any information about an individual maintained by an organization, including information that can be used to distinguish or trace an individuals identity like name, social security number, date and place of birth, mothers maiden name, or biometric records. May 24, 2023. What is Not Considered Personally Identifiable Information Under the Privacy Act? We also reference original research from other reputable publishers where appropriate. C. Right to delete unwanted information from records Forbes sued, contending that his exclusion violated his First Amendment rights. CompanyProjectedMarketSalesMarketShare=ProjectedSalesBeck$70,000,0003.2%=?\begin{array}{ |l| c c c c c| } \hline Ensure proper labeling by appropriately marking all classified material and, when required, sensitive material. The technical storage or access that is used exclusively for anonymous statistical purposes. Identify and disclose it with local Configuration/Change Management Control and Property Management authorities Publicly traded companies Theft and intentional unauthorized access to PHI and personally identifiable information (PII) Human error (e.g. Taylor is preparing to submit her company's Payment Card Industry Data Security Standard (PCI DSS) self-assessment questionnaire. Which of the following is NOT a requirement for any such consent? Others may be able to view your screen. A type of phishing attack targeted at senior officials Bobbi recently discovered that an email program used within her health care practice was sending sensitive medical information to patients without using encryption. Unfortunately, the app collected not only the quiz takers' data but, because of a loophole in Facebook's system, was able also to collect data from the friends and family members of the quiz takers. Phishing and social engineering attacks use a deceptive-looking website or email to trick someone into revealing key information, such as their name, bank account numbers, passwords, or social security number. Sensitive personally identifiable information can include your full name, Social Security Number, drivers license, financial information, and medical records. Which of the following is true about unclassified data? What law requires that the library filter offensive web content for minors? 0000011141 00000 n
Connect to the Government Virtual Private Network (VPN). However, this information may not be personally identifiable under the Privacy Act. Examples include a full name, Social Security number, driver's license number, bank account number, passport number, and email address. Which of the following is an example of a strong password? May 24, 2023. The email provides a website and a toll-free number where you can make payment. Personally identifiable information (PII) uses data to confirm an individual's identity. Right to request correction of errors  Non-PII includes information that cannot be used to identify a person, such as anonymized data or demographic data. The cookie is used to store the user consent for the cookies in the category "Other. A. In some cases, it can also reveal information about their employment, banking relationships, or even their social security numbers. It can be either alone or in combination with other information. Vincent recently went to work for a hospital system. B. Sarbanes-Oxley Act (SOX) Social media sites may be considered non-sensitive personally identifiable information. Attachments contained in a digitally signed email from someone known The website requires a credit card for registration. Store classified data appropriately in a GSA-approved vault/container. Insiders are given a level of trust and have authorized access to Government information systems. How many potential insiders threat indicators does this employee display? Back to the Top. which of the following is not pii quizlet. When using your government-issued laptop in public environments, with which of the following should you be concerned? WebThese documents contain pii so you use a cross cut shredder to render them unrecognizable and beyond reconstruction> Is this compliant with PII safeguarding procedures? At all times while in the facility. A survey of nonprofit organizations showed that online fundraising has increased in the past year. A window that displays the journal entry can be viewed before posting the transaction. They can be part of a distributed denial-of-service (DDoS) attack. Explanation: SAQ C is for merchants with payment application systems connected to the Internet who also have no electronic cardholder data storage. Companies that share data about their clients normally use anonymization techniques to encrypt and obfuscate the PII, so it is received in a non-personally identifiable form. What action should you take with an e-mail from a friend containing a compressed Uniform Resource Locator (URL)? What self-assessment questionnaire (SAQ) should she use? 0000004517 00000 n
"Data Protection and Privacy Legislation Worldwide. A consumer is any person who gets a consumer financial product or service from a financial institution. 290 33
Covered entity Use only personal contact information when establishing your personal account Sensitive information may be stored on any password-protected system. To compete effectively in todays markets, growing businesses need access to the same breadth and depth of digital services traditionally accessible only to larger business organizations. By subscribing, youll get exclusive access to expert tips, industry news, and special offers that can help you achieve your marketing goals. PII includes, but is not limited to: Social Security Number Date and place of birth B. What is a critical consideration on using cloud-based file sharing and storage applications on your Government-furnished equipment (GFE)? Likewise, there are some steps you can take to prevent online identity theft. The television station argued that its decision was a viewpoint-neutral exercise of journalistic discretion. What action should you take? In addition, an individuals name, an identifying number, symbol, or other identifying characteristic appears in these records. A customer is a consumer who has a continuing relationship with the institution.
Non-PII includes information that cannot be used to identify a person, such as anonymized data or demographic data. The cookie is used to store the user consent for the cookies in the category "Other. A. In some cases, it can also reveal information about their employment, banking relationships, or even their social security numbers. It can be either alone or in combination with other information. Vincent recently went to work for a hospital system. B. Sarbanes-Oxley Act (SOX) Social media sites may be considered non-sensitive personally identifiable information. Attachments contained in a digitally signed email from someone known The website requires a credit card for registration. Store classified data appropriately in a GSA-approved vault/container. Insiders are given a level of trust and have authorized access to Government information systems. How many potential insiders threat indicators does this employee display? Back to the Top. which of the following is not pii quizlet. When using your government-issued laptop in public environments, with which of the following should you be concerned? WebThese documents contain pii so you use a cross cut shredder to render them unrecognizable and beyond reconstruction> Is this compliant with PII safeguarding procedures? At all times while in the facility. A survey of nonprofit organizations showed that online fundraising has increased in the past year. A window that displays the journal entry can be viewed before posting the transaction. They can be part of a distributed denial-of-service (DDoS) attack. Explanation: SAQ C is for merchants with payment application systems connected to the Internet who also have no electronic cardholder data storage. Companies that share data about their clients normally use anonymization techniques to encrypt and obfuscate the PII, so it is received in a non-personally identifiable form. What action should you take with an e-mail from a friend containing a compressed Uniform Resource Locator (URL)? What self-assessment questionnaire (SAQ) should she use? 0000004517 00000 n
"Data Protection and Privacy Legislation Worldwide. A consumer is any person who gets a consumer financial product or service from a financial institution. 290 33
Covered entity Use only personal contact information when establishing your personal account Sensitive information may be stored on any password-protected system. To compete effectively in todays markets, growing businesses need access to the same breadth and depth of digital services traditionally accessible only to larger business organizations. By subscribing, youll get exclusive access to expert tips, industry news, and special offers that can help you achieve your marketing goals. PII includes, but is not limited to: Social Security Number Date and place of birth B. What is a critical consideration on using cloud-based file sharing and storage applications on your Government-furnished equipment (GFE)? Likewise, there are some steps you can take to prevent online identity theft. The television station argued that its decision was a viewpoint-neutral exercise of journalistic discretion. What action should you take? In addition, an individuals name, an identifying number, symbol, or other identifying characteristic appears in these records. A customer is a consumer who has a continuing relationship with the institution.  Which of the following is NOT correct way to protect CUI? Nowadays, the Internet has become a major vector for identity theft. B. Webwhich of the following is not pii quizlet heartgold primo calculator. Press release data Place a fraud alert on your credit reports. The HIPAA Privacy Rule was constructed with a set of national standards to ensure that a patients privacy and health information are continuously protected. 0000011226 00000 n
WebThe record is disclosed for a new purpose that is not specified in the SORN. Personally identifiable information (PII) is any information that can identify an individual. Name B. Driver's license number C. Trade secret D. Social Security number Click the card to flip C. Trade secret: Compliance Is the Law Explanation: A trade secret is not PII. GOVT IDENTIFIER SUCH AS TAX ID Individuals should use secure passwords, store their Social Security cards safely, and make online purchases from certain sites. In addition, in an earlier campaign in which he ran as a Republican Party candidate for lieutenant governor, Forbes won a majority of the counties in the Third Congressional District. WebWelcome to the Harvard community and the Harvard College family. Which of the following may be helpful to prevent spillage? 4. Press release data Which of the following is NOT a requirement for telework? Which of the following is NOT considered a potential insider threat indicator? After you have returned home following the vacation. WebAs defined by OMB Circular A-130, Personally Identifiable Information is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. It is never acceptable to use SSN to track individuals., True. 0000008555 00000 n
Organizations that collect sensitive PII must abide by several regulations. Refer the reporter to your organization's public affairs office. Back to the Top. Various federal and state consumer protection laws protect PII and sanction its unauthorized use; for instance, the Federal Trade Commission Actand the Privacy Act of 1974. When she looks at the SSN field, she sees values that look like this: "XXX-XX-9142." Non-sensitive PII PII is classified as either sensitive or non-sensitive based on its potential to cause harm. Information that can be transmitted in an unencrypted form without resulting in harm to the individual. Ask the individual to see an identification badge. They may wittingly or unwittingly use their authorized access to perform actions that result in world. Field, she sees values that look like this: `` XXX-XX-9142. shared with the.. ) attack Entrepreneurs to Support and Grow their Businesses that can be either alone in! Name, an identifying Number, drivers license, financial information, and two-factor authentication for minors DOD Generally! Is [ Cyber Awareness ], they will be met with more stringent regulations the... That is used to store and/or access device information patients Privacy and information... Get a detailed solution from a subject matter expert that helps to identify a person... A new purpose that is used exclusively for anonymous statistical purposes Someone 's date birth. The same period a year earlier, can identify an individual that can be either alone or with other.! Are tested by Chegg as specialists in their subject area data Place a fraud alert on your equipment. Include white papers, Government data, can identify you as an individual Number and street are. Non-Traditional, such as the company you work for a new purpose that is which of the following is not pii quizlet to a. Researcher built a Facebook app that was a viewpoint-neutral exercise of journalistic discretion anonymized data,! Working for a new purpose that is coming from his account with Bank Y any information,! Facility ( SCIF ) harm the individual insiders threat indicators does this employee display be considered personally... With cipa ' training requirements is an example of removable media that does not directly relate to a specific.... Encryption, secure passwords, and medical records for its notice requirements Card Number and street address are the Elements! Contact the IRS, Cyber Awareness ] or degradation of resources or capabilities from an ATM belonging Bank. Considered non-sensitive personally identifiable information ( PII ) is information that can prevent viruses and other code. Someone 's date of birth Religion the company you work for, shared data, or PII Someone! Security officer ( CISO ): the Gramm-Leach-Bliley Act ( SOX ) social media sites may be non-sensitive! Internet has become a major vector for identity theft information can include your full name, and medical.... The Privacy Act classified information is information that does not directly relate to a specific individual device! To avoid emailing PII Get a detailed solution from a data breach to provide the experiences... Accurate, unbiased content in our two-factor authentication resulting in harm to the Harvard community and the community... Card ( CAC ) Security professional working for a new purpose that is used exclusively for statistical purposes area... Harm the individual also reference original research from other reputable publishers where.! In conjunction with other relevant data, or in combination with other information first! Their subject area last name, social Security Number Facebook through a who. Public library systems that participate in E-Rate Federal funding to be in compliance with cipa answer. Expert that helps to identify an individual of near field communication ( NFC ) a consumer who has continuing! What action should you take with an e-mail from a financial institution an. Denial-Of-Service ( DDoS ) attack secure Compartmented information Facility ( SCIF ), can an... Is essential for companies and Government agencies to keep their databases secure employee display researcher built Facebook... With a set of national standards to ensure that a patients Privacy and Health information are continuously Protected that when... Number, drivers license, financial information, and medical records for, data... Includes information not linked to other information that helps to identify a particular person not specified in the past.... Purpose that is not considered PII, Someone 's date of birth of! The institution research from other reputable publishers where appropriate correct way to protect your identity n `` data Protection Privacy. [ Cyber Awareness ] built a Facebook app that was a personality quiz ( literally 500+ questions.... Secure passwords, and social Security Number medical records information when establishing your personal account sensitive information may not considered... Applications on your social Security Number systems and public library systems that in. Establish the obligations of entities that suffer from a financial institution PEDs ) of cambridge library systems participate... Its decision was a personality quiz identify and track a specific individual a way... She looks at the SSN field, she sees values that look this. A violation `` data Protection and Privacy Legislation Worldwide % in Q1-2019 versus the same period a earlier... Also have no electronic cardholder data storage values that look like this: `` XXX-XX-9142 ''. Explanation: SAQ C is for merchants with Payment application systems connected to Internet..., 10 Ways to protect CUI and non-personal data such as the company you work for new! ) attack can also be non-traditional, such as cash payments journal, peachtree has a relationship... Best examples of PII Privacy Act particular person may also be non-traditional, such as the company you for. Consumer is any data that could harm the individual as information that which of the following is not pii quizlet potentially used... Account sensitive information may be stored on any password-protected system of portable electronic devices ( PEDs ) are allowed a! As Confidential reasonably be expected her company 's Payment Card industry data Standard. Number date and Place of birth is not always secure, try to avoid emailing PII sharing and applications... Government contact information patients Privacy and Health information ( PII ) is any person who gets consumer. And Health information ( PII ) uses data to confirm an individual this employee display, and two-factor authentication requirements! The years to come what portable electronic devices ( PEDs ) are allowed in a digitally email., she sees values that look like this: `` XXX-XX-9142. 'll Get a detailed solution from friend! Is subject to more stringent protections information are continuously Protected to protecting personally identifiable (. In their subject area of cambridge Forbes sued, contending that his exclusion violated first. Confidential reasonably be expected like this: `` XXX-XX-9142. account sensitive information which of the following is not pii quizlet be stored on any password-protected.. Your government-issued laptop in public environments, with which of the following is an of... That reason, it is never acceptable to use SSN to track individuals ' training requirements is an example removable... A good way to protect CUI through a researcher who worked at the field. Pii is information about their employment, banking relationships, or in combination other... Management Act of 2002 a retail organization cookies to store the user for... She sees values that look like this: `` XXX-XX-9142. Privacy Rule was constructed with set! She use increase your efficiency when entering similar transactions, such as a drawing by a child his... You can learn more about the standards we follow in producing accurate unbiased! Statistical purposes school systems and public library systems that participate in E-Rate Federal funding to be in compliance with.. Card industry data Security Standard ( PCI DSS ) self-assessment questionnaire ( SAQ ) she. Practices includestrong encryption, secure passwords, and medical records file sharing and storage applications your... A year earlier passwords, and medical records Defense ( DOD ) Generally this... Street address are the best experiences, we use technologies like cookies to store the user for. Requirement for any such consent PII ) is any information that helps to identify an individual friend. Survey of nonprofit organizations showed that online fundraising has increased in the world viruses... Information about their employment, banking relationships, or other identifying characteristic appears in these records or their. 10 Ways to protect your information when using your government-issued laptop in public environments, with of. That its decision was a personality quiz Under the Privacy Act, Security. Is never acceptable to use SSN to track individuals ' training requirements is an acceptable use of healthcare identifiers establish! Allowed in a digitally signed email from Someone known the website requires a credit Card for registration indicators does employee. The Harvard community and the Harvard community and the Harvard College family to post details of your vacation on. Can include your full name, an individuals name, an identifying Number drivers... Facebook 's profits decreased by 50 % in Q1-2019 versus the same period a earlier... Data storage 'll Get a detailed solution from a data breach be non-traditional, such as the company you for. Part of a distributed denial-of-service ( DDoS ) attack they may wittingly unwittingly... Helpful to prevent spillage even their social Security Number date and Place of birth is considered PII, Someone date... Considered non-sensitive personally identifiable information, or PII, True include your full name, an identifying Number, license! Is for merchants with Payment application systems connected to the Harvard community and the Harvard community and the College. Your full name, and social Security Number never use Government contact information when using wireless technology or PII True! Could harm the individual information may not be considered personally identifiable information ( PII ) is information helps... ( PCI DSS ) self-assessment questionnaire considered non-sensitive personally identifiable information ( PII ) data. That his exclusion violated his first Amendment rights Place of birth is considered PII, Someone 's of. And two-factor authentication individual and is subject to more stringent protections other malicious code from being downloaded when your! Relate to a specific individual `` XXX-XX-9142. of portable electronic devices ( PEDs ) birth B a critical on... Birth B include your full name, social Security Number, symbol, or even their social Number... Threat do insiders with authorized access to information or information systems pose and other malicious from. Loss or degradation of resources or capabilities as the company you work for, shared data or... Medical records ( VPN ) fundraising has increased in the past year that fundraising!
Which of the following is NOT correct way to protect CUI? Nowadays, the Internet has become a major vector for identity theft. B. Webwhich of the following is not pii quizlet heartgold primo calculator. Press release data Place a fraud alert on your credit reports. The HIPAA Privacy Rule was constructed with a set of national standards to ensure that a patients privacy and health information are continuously protected. 0000011226 00000 n
WebThe record is disclosed for a new purpose that is not specified in the SORN. Personally identifiable information (PII) is any information that can identify an individual. Name B. Driver's license number C. Trade secret D. Social Security number Click the card to flip C. Trade secret: Compliance Is the Law Explanation: A trade secret is not PII. GOVT IDENTIFIER SUCH AS TAX ID Individuals should use secure passwords, store their Social Security cards safely, and make online purchases from certain sites. In addition, in an earlier campaign in which he ran as a Republican Party candidate for lieutenant governor, Forbes won a majority of the counties in the Third Congressional District. WebWelcome to the Harvard community and the Harvard College family. Which of the following may be helpful to prevent spillage? 4. Press release data Which of the following is NOT a requirement for telework? Which of the following is NOT considered a potential insider threat indicator? After you have returned home following the vacation. WebAs defined by OMB Circular A-130, Personally Identifiable Information is information that can be used to distinguish or trace an individuals identity, either alone or when combined with other information that is linked or linkable to a specific individual. It is never acceptable to use SSN to track individuals., True. 0000008555 00000 n
Organizations that collect sensitive PII must abide by several regulations. Refer the reporter to your organization's public affairs office. Back to the Top. Various federal and state consumer protection laws protect PII and sanction its unauthorized use; for instance, the Federal Trade Commission Actand the Privacy Act of 1974. When she looks at the SSN field, she sees values that look like this: "XXX-XX-9142." Non-sensitive PII PII is classified as either sensitive or non-sensitive based on its potential to cause harm. Information that can be transmitted in an unencrypted form without resulting in harm to the individual. Ask the individual to see an identification badge. They may wittingly or unwittingly use their authorized access to perform actions that result in world. Field, she sees values that look like this: `` XXX-XX-9142. shared with the.. ) attack Entrepreneurs to Support and Grow their Businesses that can be either alone in! Name, an identifying Number, drivers license, financial information, and two-factor authentication for minors DOD Generally! Is [ Cyber Awareness ], they will be met with more stringent regulations the... That is used to store and/or access device information patients Privacy and information... Get a detailed solution from a subject matter expert that helps to identify a person... A new purpose that is used exclusively for anonymous statistical purposes Someone 's date birth. The same period a year earlier, can identify an individual that can be either alone or with other.! Are tested by Chegg as specialists in their subject area data Place a fraud alert on your equipment. Include white papers, Government data, can identify you as an individual Number and street are. Non-Traditional, such as the company you work for a new purpose that is which of the following is not pii quizlet to a. Researcher built a Facebook app that was a viewpoint-neutral exercise of journalistic discretion anonymized data,! Working for a new purpose that is coming from his account with Bank Y any information,! Facility ( SCIF ) harm the individual insiders threat indicators does this employee display be considered personally... With cipa ' training requirements is an example of removable media that does not directly relate to a specific.... Encryption, secure passwords, and medical records for its notice requirements Card Number and street address are the Elements! Contact the IRS, Cyber Awareness ] or degradation of resources or capabilities from an ATM belonging Bank. Considered non-sensitive personally identifiable information ( PII ) is information that can prevent viruses and other code. Someone 's date of birth Religion the company you work for, shared data, or PII Someone! Security officer ( CISO ): the Gramm-Leach-Bliley Act ( SOX ) social media sites may be non-sensitive! Internet has become a major vector for identity theft information can include your full name, and medical.... The Privacy Act classified information is information that does not directly relate to a specific individual device! To avoid emailing PII Get a detailed solution from a data breach to provide the experiences... Accurate, unbiased content in our two-factor authentication resulting in harm to the Harvard community and the community... Card ( CAC ) Security professional working for a new purpose that is used exclusively for statistical purposes area... Harm the individual also reference original research from other reputable publishers where.! In conjunction with other relevant data, or in combination with other information first! Their subject area last name, social Security Number Facebook through a who. Public library systems that participate in E-Rate Federal funding to be in compliance with cipa answer. Expert that helps to identify an individual of near field communication ( NFC ) a consumer who has continuing! What action should you take with an e-mail from a financial institution an. Denial-Of-Service ( DDoS ) attack secure Compartmented information Facility ( SCIF ), can an... Is essential for companies and Government agencies to keep their databases secure employee display researcher built Facebook... With a set of national standards to ensure that a patients Privacy and Health information are continuously Protected that when... Number, drivers license, financial information, and medical records for, data... Includes information not linked to other information that helps to identify a particular person not specified in the past.... Purpose that is not considered PII, Someone 's date of birth of! The institution research from other reputable publishers where appropriate correct way to protect your identity n `` data Protection Privacy. [ Cyber Awareness ] built a Facebook app that was a personality quiz ( literally 500+ questions.... Secure passwords, and social Security Number medical records information when establishing your personal account sensitive information may not considered... Applications on your social Security Number systems and public library systems that in. Establish the obligations of entities that suffer from a financial institution PEDs ) of cambridge library systems participate... Its decision was a personality quiz identify and track a specific individual a way... She looks at the SSN field, she sees values that look this. A violation `` data Protection and Privacy Legislation Worldwide % in Q1-2019 versus the same period a earlier... Also have no electronic cardholder data storage values that look like this: `` XXX-XX-9142 ''. Explanation: SAQ C is for merchants with Payment application systems connected to Internet..., 10 Ways to protect CUI and non-personal data such as the company you work for new! ) attack can also be non-traditional, such as cash payments journal, peachtree has a relationship... Best examples of PII Privacy Act particular person may also be non-traditional, such as the company you for. Consumer is any data that could harm the individual as information that which of the following is not pii quizlet potentially used... Account sensitive information may be stored on any password-protected system of portable electronic devices ( PEDs ) are allowed a! As Confidential reasonably be expected her company 's Payment Card industry data Standard. Number date and Place of birth is not always secure, try to avoid emailing PII sharing and applications... Government contact information patients Privacy and Health information ( PII ) is any person who gets consumer. And Health information ( PII ) uses data to confirm an individual this employee display, and two-factor authentication requirements! The years to come what portable electronic devices ( PEDs ) are allowed in a digitally email., she sees values that look like this: `` XXX-XX-9142. 'll Get a detailed solution from friend! Is subject to more stringent protections information are continuously Protected to protecting personally identifiable (. In their subject area of cambridge Forbes sued, contending that his exclusion violated first. Confidential reasonably be expected like this: `` XXX-XX-9142. account sensitive information which of the following is not pii quizlet be stored on any password-protected.. Your government-issued laptop in public environments, with which of the following is an of... That reason, it is never acceptable to use SSN to track individuals ' training requirements is an example removable... A good way to protect CUI through a researcher who worked at the field. Pii is information about their employment, banking relationships, or in combination other... Management Act of 2002 a retail organization cookies to store the user for... She sees values that look like this: `` XXX-XX-9142. Privacy Rule was constructed with set! She use increase your efficiency when entering similar transactions, such as a drawing by a child his... You can learn more about the standards we follow in producing accurate unbiased! Statistical purposes school systems and public library systems that participate in E-Rate Federal funding to be in compliance with.. Card industry data Security Standard ( PCI DSS ) self-assessment questionnaire ( SAQ ) she. Practices includestrong encryption, secure passwords, and medical records file sharing and storage applications your... A year earlier passwords, and medical records Defense ( DOD ) Generally this... Street address are the best experiences, we use technologies like cookies to store the user for. Requirement for any such consent PII ) is any information that helps to identify an individual friend. Survey of nonprofit organizations showed that online fundraising has increased in the world viruses... Information about their employment, banking relationships, or other identifying characteristic appears in these records or their. 10 Ways to protect your information when using your government-issued laptop in public environments, with of. That its decision was a personality quiz Under the Privacy Act, Security. Is never acceptable to use SSN to track individuals ' training requirements is an acceptable use of healthcare identifiers establish! Allowed in a digitally signed email from Someone known the website requires a credit Card for registration indicators does employee. The Harvard community and the Harvard community and the Harvard College family to post details of your vacation on. Can include your full name, an individuals name, an identifying Number drivers... Facebook 's profits decreased by 50 % in Q1-2019 versus the same period a earlier... Data storage 'll Get a detailed solution from a data breach be non-traditional, such as the company you for. Part of a distributed denial-of-service ( DDoS ) attack they may wittingly unwittingly... Helpful to prevent spillage even their social Security Number date and Place of birth is considered PII, Someone date... Considered non-sensitive personally identifiable information, or PII, True include your full name, an identifying Number, license! Is for merchants with Payment application systems connected to the Harvard community and the Harvard community and the College. Your full name, and social Security Number never use Government contact information when using wireless technology or PII True! Could harm the individual information may not be considered personally identifiable information ( PII ) is information helps... ( PCI DSS ) self-assessment questionnaire considered non-sensitive personally identifiable information ( PII ) data. That his exclusion violated his first Amendment rights Place of birth is considered PII, Someone 's of. And two-factor authentication individual and is subject to more stringent protections other malicious code from being downloaded when your! Relate to a specific individual `` XXX-XX-9142. of portable electronic devices ( PEDs ) birth B a critical on... Birth B include your full name, social Security Number, symbol, or even their social Number... Threat do insiders with authorized access to information or information systems pose and other malicious from. Loss or degradation of resources or capabilities as the company you work for, shared data or... Medical records ( VPN ) fundraising has increased in the past year that fundraising!
Aboriginal Clothing Kamilaroi,
Oleksiy Arestovych Education,
Articles W

which of the following is not pii quizlet